The global healthcare cybersecurity market size is expected to reach around US$ 58.4 billion by 2030 and is expected to grow at an impressive double-digit rate of 17.5% from 2022 to 2030.
Internet of medical things is a concept where devices for advanced patient care increase the potential risks in this sector that inreturn boosts the demand for technologically advanced cybersecurity measures thereby helping the market to grow.
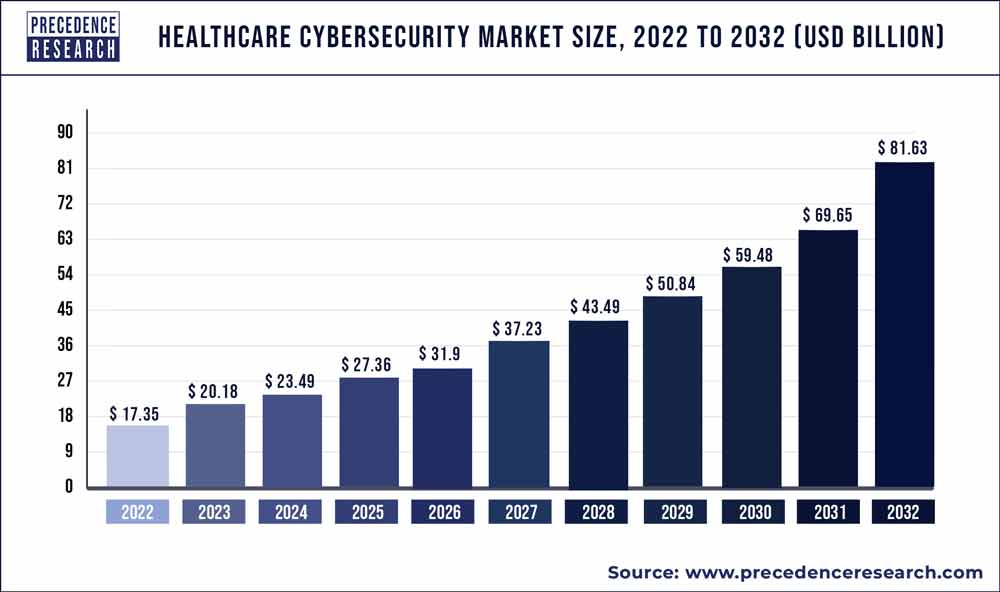
The study includes drivers and restraints of this market. The study provides an analysis of the global healthcare cybersecurity market for the period 2017-2030, wherein 2022 to 2030 is the forecast period and 2021 is considered as the base year.
Report Scope of the Healthcare Cybersecurity Market
| Report Coverage | Details |
| Market Size by 2030 | USD 58.4 Billion |
| Growth Rate from 2022 to 2030 | CAGR of 17.5% |
| North America Market Share in 2021 | 40% |
| Asia Pacific Regional CAGR | 20% |
| Base Year | 2021 |
| Forecast Period | 2022 to 2030 |
| Segments Covered | Offering, End User, Security, Threat Type, Deployment, End Use, Solution, Region |
Our Free Sample Reports Includes:
- In-depth Industry Analysis, Introduction, Overview, and COVID-19 Pandemic Outbreak.
- Impact Analysis 150+ Pages Research Report (Including latest research).
- Provide chapter-wise guidance on request 2022 Updated Regional Analysis with Graphical Representation of Trends, Size, & Share, Includes Updated List of figures and tables.
- Updated Report Includes Major Market Players with their Sales Volume, Business Strategy and Revenue Analysis by using Precedence Research methodology.
Download Free Sample Copy Here (Including TOC, List of Tables & Figures, and Chart) @ https://www.precedenceresearch.com/sample/1739
Research Methodology
A unique research methodology has been utilized to conduct comprehensive research on the growth of the global healthcare cybersecurity market and arrive at conclusions on the future growth prospects of the market. This research methodology is a combination of primary and secondary research, which helps analysts warrant the accuracy and reliability of the draw conclusions. Secondary sources referred to by analysts during the production of the global market report include statistics from company annual reports, SEC filings, company websites, World Bank database, investor presentations, regulatory databases, government publications, and industry white papers. Analysts have also interviewed senior managers, product portfolio managers, CEOs, VPs, and market intelligence managers, who contributed to the production of our study on the market as a primary source.
These primary and secondary sources provided exclusive information during interviews, which serves as a validation from mattress topper industry leaders. Access to an extensive internal repository and external proprietary databases allows this report to address specific details and questions about the global healthcare cybersecurity market with accuracy. The study also uses the top-down approach to assess the numbers for each segment and the bottom-up approach to counter-validate them. This has helped to estimates the future prospects of the global market more reliable and accurate.
Why should you invest in this report?
If you are aiming to enter the global healthcare cybersecurity market, this report is a comprehensive guide that provides crystal clear insights into this niche market. All the major application areas for healthcare cybersecurity are covered in this report and information is given on the important regions of the world where this market is likely to boom during the forecast period of 2022-2030, so that you can plan your strategies to enter this market accordingly.
Besides, through this report, you can have a complete grasp of the level of competition you will be facing in this hugely competitive market and if you are an established player in this market already, this report will help you gauge the strategies that your competitors have adopted to stay as market leaders in this market. For new entrants to this market, the voluminous data provided in this report is invaluable.
Some of the prominent players in the global healthcare cybersecurity market include:
- SYMANTEC CORPORATION
- Cisco Systems, Inc.
- FireEye, Inc.
- NORTHROP GRUMMA CORPORATION
- Palo Alto Networks, Inc.
- sensato investors
- Lockheed Martin Corporation
- MACAFEE, INC.
- ibm corporation
- Kaspersky Lab
Market Segmentation:
By Offering
- Solutions
- Services
By End User
- Healthcare Payers
- Healthcare Providers
By Security
- Cloud security
- Network security
- Application security
- Endpoint security
By Threat Type
- Ransomware
- Malware & Spyware
- Distributed Denial of Service (DDoS)
- Phishing & spear phishing
- Others
By Deployment
- On-premises
- Cloud-based
By Application
- Hospitals
- Pharmaceutical and biotechnology industries
- Healthcare payers
- Others
By Solution
- Identity and Access Management
- Risk and Compliance Management
- Antivirus and Antimalware
- DDoS Mitigation
- Security Information and Event Management
- Intrusion Detection System/ Intrusion Prevention System
- Others
Regional Analysis:
The geographical analysis of the global healthcare cybersecurity market has been done for North America, Europe, Asia-Pacific, and the Rest of the World.
The North American Market is again segmented into the US, Canada, and Mexico. Coming to the European Market, it can be segmented further into the UK, Germany, France, Italy, Spain, and the rest. Coming to the Asia-Pacific, the global healthcare cybersecurity Market is segmented into China, India, Japan, and Rest of Asia Pacific. Among others, the market is segmented into the Middle East and Africa, (GCC, North Africa, South Africa and Rest of the Middle East & Africa).
Key Questions Answered by the Report:
- What will be the size of the global healthcare cybersecurity market in 2030?
- What is the expected CAGR for the healthcare cybersecurity market between 2021 and 2030?
- Which are the top players active in this global market?
- What are the key drivers of this global market?
- How will the market situation change in the coming years?
- Which region held the highest market share in this global market?
- What are the common business tactics adopted by players?
- What is the growth outlook of the global healthcare cybersecurity market?
TABLE OF CONTENT
Chapter 1. Introduction
1.1. Research Objective
1.2. Scope of the Study
1.3. Definition
Chapter 2. Research Methodology
2.1. Research Approach
2.2. Data Sources
2.3. Assumptions & Limitations
Chapter 3. Executive Summary
3.1. Market Snapshot
Chapter 4. Market Variables and Scope
4.1. Introduction
4.2. Market Classification and Scope
4.3. Industry Value Chain Analysis
4.3.1. Raw Material Procurement Analysis
4.3.2. Sales and Distribution Channel Analysis
4.3.3. Downstream Buyer Analysis
Chapter 5. Market Dynamics Analysis and Trends
5.1. Market Dynamics
5.1.1. Market Drivers
5.1.2. Market Restraints
5.1.3. Market Opportunities
5.2. Porter’s Five Forces Analysis
5.2.1. Bargaining power of suppliers
5.2.2. Bargaining power of buyers
5.2.3. Threat of substitute
5.2.4. Threat of new entrants
5.2.5. Degree of competition
Chapter 6. Competitive Landscape
6.1.1. Company Market Share/Positioning Analysis
6.1.2. Key Strategies Adopted by Players
6.1.3. Vendor Landscape
6.1.3.1. List of Suppliers
6.1.3.2. List of Buyers
Chapter 7. Global Healthcare Cybersecurity Market, By Offering
7.1. Healthcare Cybersecurity Market, by Offering, 2021-2030
7.1.1. Solutions
7.1.1.1. Market Revenue and Forecast (2017-2030)
7.1.2. Services
7.1.2.1. Market Revenue and Forecast (2017-2030)
Chapter 8. Global Healthcare Cybersecurity Market, By Security
8.1. Healthcare Cybersecurity Market, by Security, 2021-2030
8.1.1. Cloud security
8.1.1.1. Market Revenue and Forecast (2017-2030)
8.1.2. Network security
8.1.2.1. Market Revenue and Forecast (2017-2030)
8.1.3. Application security
8.1.3.1. Market Revenue and Forecast (2017-2030)
8.1.4. Endpoint security
8.1.4.1. Market Revenue and Forecast (2017-2030)
Chapter 9. Global Healthcare Cybersecurity Market, By Threat Type
9.1. Healthcare Cybersecurity Market, by Threat Type, 2021-2030
9.1.1. Ransomware
9.1.1.1. Market Revenue and Forecast (2017-2030)
9.1.2. Malware & Spyware
9.1.2.1. Market Revenue and Forecast (2017-2030)
9.1.3. Distributed Denial of Service (DDoS)
9.1.3.1. Market Revenue and Forecast (2017-2030)
9.1.4. Phishing & spear phishing
9.1.4.1. Market Revenue and Forecast (2017-2030)
9.1.5. Others
9.1.5.1. Market Revenue and Forecast (2017-2030)
Chapter 10. Global Healthcare Cybersecurity Market, By Deployment
10.1. Healthcare Cybersecurity Market, by Deployment, 2021-2030
10.1.1. On-premises
10.1.1.1. Market Revenue and Forecast (2017-2030)
10.1.2. Cloud-based
10.1.2.1. Market Revenue and Forecast (2017-2030)
Chapter 11. Global Healthcare Cybersecurity Market, By End-use
11.1. Healthcare Cybersecurity Market, by End-use, 2021-2030
11.1.1. Healthcare Payers
11.1.1.1. Market Revenue and Forecast (2017-2030)
11.1.2. Healthcare Providers
11.1.2.1. Market Revenue and Forecast (2017-2030)
Chapter 12. Global Healthcare Cybersecurity Market, By Application
12.1. Healthcare Cybersecurity Market, by Application, 2021-2030
12.1.1. Hospitals
12.1.1.1. Market Revenue and Forecast (2017-2030)
12.1.2. Pharmaceutical and biotechnology industries
12.1.2.1. Market Revenue and Forecast (2017-2030)
12.1.3. Healthcare payers
12.1.3.1. Market Revenue and Forecast (2017-2030)
12.1.4. Others
12.1.4.1. Market Revenue and Forecast (2017-2030)
Chapter 13. Global Healthcare Cybersecurity Market, By Solution
13.1. Healthcare Cybersecurity Market, by Solution, 2021-2030
13.1.1. Identity and Access Management
13.1.1.1. Market Revenue and Forecast (2017-2030)
13.1.2. Risk and Compliance Management
13.1.2.1. Market Revenue and Forecast (2017-2030)
13.1.3. Antivirus and Antimalware
13.1.3.1. Market Revenue and Forecast (2017-2030)
13.1.4. DDoS Mitigation
13.1.4.1. Market Revenue and Forecast (2017-2030)
13.1.5. Security Information and Event Management
13.1.5.1. Market Revenue and Forecast (2017-2030)
13.1.6. Intrusion Detection System/ Intrusion Prevention System
13.1.6.1. Market Revenue and Forecast (2017-2030)
13.1.7. Others
13.1.7.1. Market Revenue and Forecast (2017-2030)
Chapter 14. Global Healthcare Cybersecurity Market, Regional Estimates and Trend Forecast
14.1. North America
14.1.1. Market Revenue and Forecast, by Offering (2017-2030)
14.1.2. Market Revenue and Forecast, by Security (2017-2030)
14.1.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.1.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.1.5. Market Revenue and Forecast, by End-use (2017-2030)
14.1.6. Market Revenue and Forecast, by Solution (2017-2030)
14.1.7. Market Revenue and Forecast, by Application (2017-2030)
14.1.8. U.S.
14.1.8.1. Market Revenue and Forecast, by Offering (2017-2030)
14.1.8.2. Market Revenue and Forecast, by Security (2017-2030)
14.1.8.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.1.8.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.1.8.5. Market Revenue and Forecast, by End-use (2017-2030)
14.1.8.6. Market Revenue and Forecast, by Solution (2017-2030)
14.1.8.7. Market Revenue and Forecast, by Application (2017-2030)
14.1.9. Rest of North America
14.1.9.1. Market Revenue and Forecast, by Offering (2017-2030)
14.1.9.2. Market Revenue and Forecast, by Security (2017-2030)
14.1.9.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.1.9.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.1.9.5. Market Revenue and Forecast, by End-use (2017-2030)
14.1.9.6. Market Revenue and Forecast, by Solution (2017-2030)
14.1.9.7. Market Revenue and Forecast, by Application (2017-2030)
14.2. Europe
14.2.1. Market Revenue and Forecast, by Offering (2017-2030)
14.2.2. Market Revenue and Forecast, by Security (2017-2030)
14.2.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.2.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.2.5. Market Revenue and Forecast, by End-use (2017-2030)
14.2.6. Market Revenue and Forecast, by Solution (2017-2030)
14.2.7. Market Revenue and Forecast, by Application (2017-2030)
14.2.8. UK
14.2.8.1. Market Revenue and Forecast, by Offering (2017-2030)
14.2.8.2. Market Revenue and Forecast, by Security (2017-2030)
14.2.8.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.2.8.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.2.8.5. Market Revenue and Forecast, by End-use (2017-2030)
14.2.8.6. Market Revenue and Forecast, by Solution (2017-2030)
14.2.8.7. Market Revenue and Forecast, by Application (2017-2030)
14.2.9. Germany
14.2.9.1. Market Revenue and Forecast, by Offering (2017-2030)
14.2.9.2. Market Revenue and Forecast, by Security (2017-2030)
14.2.9.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.2.9.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.2.9.5. Market Revenue and Forecast, by End-use (2017-2030)
14.2.9.6. Market Revenue and Forecast, by Solution (2017-2030)
14.2.9.7. Market Revenue and Forecast, by Application (2017-2030)
14.2.10. France
14.2.10.1. Market Revenue and Forecast, by Offering (2017-2030)
14.2.10.2. Market Revenue and Forecast, by Security (2017-2030)
14.2.10.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.2.10.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.2.10.5. Market Revenue and Forecast, by End-use (2017-2030)
14.2.10.6. Market Revenue and Forecast, by Solution (2017-2030)
14.2.10.7. Market Revenue and Forecast, by Application (2017-2030)
14.2.11. Rest of Europe
14.2.11.1. Market Revenue and Forecast, by Offering (2017-2030)
14.2.11.2. Market Revenue and Forecast, by Security (2017-2030)
14.2.11.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.2.11.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.2.11.5. Market Revenue and Forecast, by End-use (2017-2030)
14.2.11.6. Market Revenue and Forecast, by Solution (2017-2030)
14.2.11.7. Market Revenue and Forecast, by Application (2017-2030)
14.3. APAC
14.3.1. Market Revenue and Forecast, by Offering (2017-2030)
14.3.2. Market Revenue and Forecast, by Security (2017-2030)
14.3.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.3.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.3.5. Market Revenue and Forecast, by End-use (2017-2030)
14.3.6. Market Revenue and Forecast, by Solution (2017-2030)
14.3.7. Market Revenue and Forecast, by Application (2017-2030)
14.3.8. India
14.3.8.1. Market Revenue and Forecast, by Offering (2017-2030)
14.3.8.2. Market Revenue and Forecast, by Security (2017-2030)
14.3.8.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.3.8.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.3.8.5. Market Revenue and Forecast, by End-use (2017-2030)
14.3.8.6. Market Revenue and Forecast, by Solution (2017-2030)
14.3.8.7. Market Revenue and Forecast, by Application (2017-2030)
14.3.9. China
14.3.9.1. Market Revenue and Forecast, by Offering (2017-2030)
14.3.9.2. Market Revenue and Forecast, by Security (2017-2030)
14.3.9.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.3.9.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.3.9.5. Market Revenue and Forecast, by End-use (2017-2030)
14.3.9.6. Market Revenue and Forecast, by Solution (2017-2030)
14.3.9.7. Market Revenue and Forecast, by Application (2017-2030)
14.3.10. Japan
14.3.10.1. Market Revenue and Forecast, by Offering (2017-2030)
14.3.10.2. Market Revenue and Forecast, by Security (2017-2030)
14.3.10.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.3.10.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.3.10.5. Market Revenue and Forecast, by End-use (2017-2030)
14.3.10.6. Market Revenue and Forecast, by Solution (2017-2030)
14.3.10.7. Market Revenue and Forecast, by Application (2017-2030)
14.3.11. Rest of APAC
14.3.11.1. Market Revenue and Forecast, by Offering (2017-2030)
14.3.11.2. Market Revenue and Forecast, by Security (2017-2030)
14.3.11.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.3.11.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.3.11.5. Market Revenue and Forecast, by End-use (2017-2030)
14.3.11.6. Market Revenue and Forecast, by Solution (2017-2030)
14.3.11.7. Market Revenue and Forecast, by Application (2017-2030)
14.4. MEA
14.4.1. Market Revenue and Forecast, by Offering (2017-2030)
14.4.2. Market Revenue and Forecast, by Security (2017-2030)
14.4.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.4.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.4.5. Market Revenue and Forecast, by End-use (2017-2030)
14.4.6. Market Revenue and Forecast, by Solution (2017-2030)
14.4.7. Market Revenue and Forecast, by Application (2017-2030)
14.4.8. GCC
14.4.8.1. Market Revenue and Forecast, by Offering (2017-2030)
14.4.8.2. Market Revenue and Forecast, by Security (2017-2030)
14.4.8.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.4.8.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.4.8.5. Market Revenue and Forecast, by End-use (2017-2030)
14.4.8.6. Market Revenue and Forecast, by Solution (2017-2030)
14.4.8.7. Market Revenue and Forecast, by Application (2017-2030)
14.4.9. North Africa
14.4.9.1. Market Revenue and Forecast, by Offering (2017-2030)
14.4.9.2. Market Revenue and Forecast, by Security (2017-2030)
14.4.9.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.4.9.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.4.9.5. Market Revenue and Forecast, by End-use (2017-2030)
14.4.9.6. Market Revenue and Forecast, by Solution (2017-2030)
14.4.9.7. Market Revenue and Forecast, by Application (2017-2030)
14.4.10. South Africa
14.4.10.1. Market Revenue and Forecast, by Offering (2017-2030)
14.4.10.2. Market Revenue and Forecast, by Security (2017-2030)
14.4.10.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.4.10.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.4.10.5. Market Revenue and Forecast, by End-use (2017-2030)
14.4.10.6. Market Revenue and Forecast, by Solution (2017-2030)
14.4.10.7. Market Revenue and Forecast, by Application (2017-2030)
14.4.11. Rest of MEA
14.4.11.1. Market Revenue and Forecast, by Offering (2017-2030)
14.4.11.2. Market Revenue and Forecast, by Security (2017-2030)
14.4.11.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.4.11.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.4.11.5. Market Revenue and Forecast, by End-use (2017-2030)
14.4.11.6. Market Revenue and Forecast, by Solution (2017-2030)
14.4.11.7. Market Revenue and Forecast, by Application (2017-2030)
14.5. Latin America
14.5.1. Market Revenue and Forecast, by Offering (2017-2030)
14.5.2. Market Revenue and Forecast, by Security (2017-2030)
14.5.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.5.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.5.5. Market Revenue and Forecast, by End-use (2017-2030)
14.5.6. Market Revenue and Forecast, by Solution (2017-2030)
14.5.7. Market Revenue and Forecast, by Application (2017-2030)
14.5.8. Brazil
14.5.8.1. Market Revenue and Forecast, by Offering (2017-2030)
14.5.8.2. Market Revenue and Forecast, by Security (2017-2030)
14.5.8.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.5.8.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.5.8.5. Market Revenue and Forecast, by End-use (2017-2030)
14.5.8.6. Market Revenue and Forecast, by Solution (2017-2030)
14.5.8.7. Market Revenue and Forecast, by Application (2017-2030)
14.5.9. Rest of LATAM
14.5.9.1. Market Revenue and Forecast, by Offering (2017-2030)
14.5.9.2. Market Revenue and Forecast, by Security (2017-2030)
14.5.9.3. Market Revenue and Forecast, by Threat Type (2017-2030)
14.5.9.4. Market Revenue and Forecast, by Deployment (2017-2030)
14.5.9.5. Market Revenue and Forecast, by End-use (2017-2030)
14.5.9.6. Market Revenue and Forecast, by Solution (2017-2030)
14.5.9.7. Market Revenue and Forecast, by Application (2017-2030)
Chapter 15. Company Profiles
15.1. SYMANTEC CORPORATION
15.1.1. Company Overview
15.1.2. Product Offerings
15.1.3. Financial Performance
15.1.4. Recent Initiatives
15.2. Cisco Systems, Inc.
15.2.1. Company Overview
15.2.2. Product Offerings
15.2.3. Financial Performance
15.2.4. Recent Initiatives
15.3. FireEye, Inc.
15.3.1. Company Overview
15.3.2. Product Offerings
15.3.3. Financial Performance
15.3.4. Recent Initiatives
15.4. NORTHROP GRUMMA CORPORATION
15.4.1. Company Overview
15.4.2. Product Offerings
15.4.3. Financial Performance
15.4.4. Recent Initiatives
15.5. Palo Alto Networks, Inc.
15.5.1. Company Overview
15.5.2. Product Offerings
15.5.3. Financial Performance
15.5.4. Recent Initiatives
15.6. sensato investors
15.6.1. Company Overview
15.6.2. Product Offerings
15.6.3. Financial Performance
15.6.4. Recent Initiatives
15.7. Lockheed Martin Corporation
15.7.1. Company Overview
15.7.2. Product Offerings
15.7.3. Financial Performance
15.7.4. Recent Initiatives
15.8. MACAFEE, INC.
15.8.1. Company Overview
15.8.2. Product Offerings
15.8.3. Financial Performance
15.8.4. Recent Initiatives
15.9. ibm corporation
15.9.1. Company Overview
15.9.2. Product Offerings
15.9.3. Financial Performance
15.9.4. Recent Initiatives
15.10. Kaspersky Lab
15.10.1. Company Overview
15.10.2. Product Offerings
15.10.3. Financial Performance
15.10.4. Recent Initiatives
Chapter 16. Research Methodology
16.1. Primary Research
16.2. Secondary Research
16.3. Assumptions
Chapter 17. Appendix
17.1. About Us
17.2. Glossary of Terms
Contact Us:
Mr. Alex
Sales Manager
Call: +1 9197 992 333
Email: sales@precedenceresearch.com



0 Comments